#computer users
Explore tagged Tumblr posts
Text
Honestly, the thing that really burns my ass about mobile web design these days isn't even the bloated ads – it's the pages where there's nowhere that's safe to touch to scroll because every single pixel is a clickable hotspot that whisks you away to somewhere else, including the text. I truly believe the owners of websites that do this should die.
#life#computers#technology#internet#web design#user interface#user experience#ux#ui#grumping#death mention#swearing
5K notes
·
View notes
Text
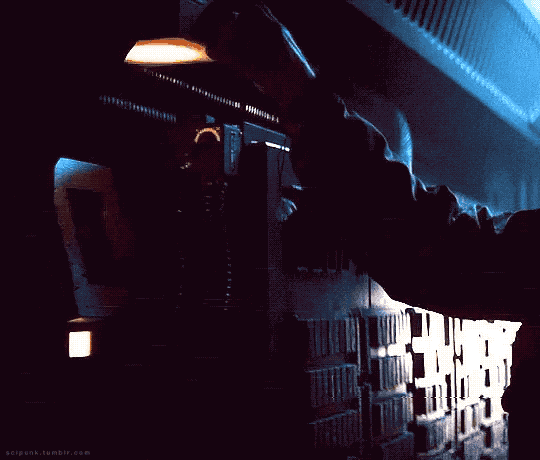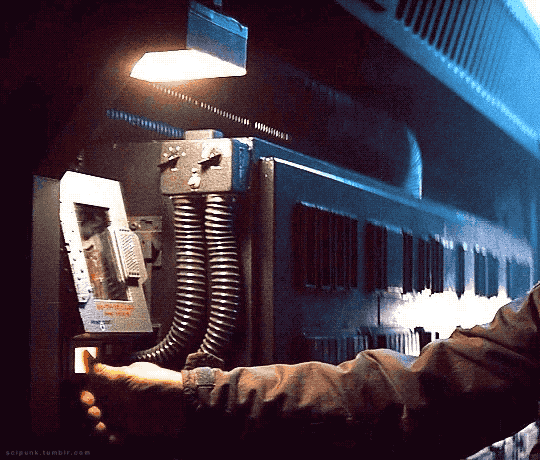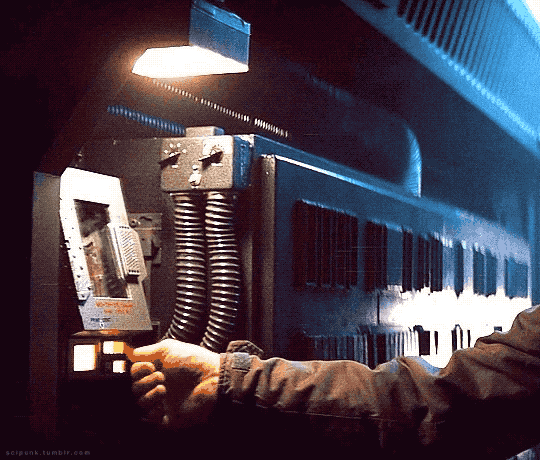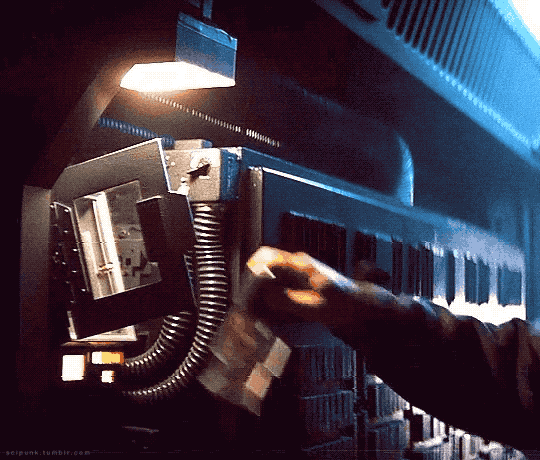








Alien (1979)
#alien movie#scifiedit#science fiction#nostromo#spaceship#interiors#spacecraft#old computers#computing#atmospheric#scifi aesthetic#cyberpunk aesthetic#graphic design#glitch#user interface#user interaction#mother#space ship#gifs#gifset
4K notes
·
View notes
Text
We ask your questions anonymously so you don’t have to! Submissions are open on the 1st and 15th of the month.
#polls#incognito polls#anonymous#tumblr polls#tumblr users#questions#polls about food#submitted mar 15#food#computers#workspace
487 notes
·
View notes
Text

Redraw of a cat meme. This is how I see baby Espio......
#espio the chameleon#sth#sonic fanart#classic espio#someone link me the original source of this i lost it and can't find it again#except on ifunny which is NOT a source#it will drive me insane not to properly credit this.... plz#anyway. the user got so distracted by tumblr that the user had to unplug the ethernet cable from their home computer to get more art done#the user is me#i miss finishing stuff to post (almost) everyday already. i want to get back to that even if it's just silly quick meme redraws#we must stay silly at all costs least we succumb to the rot#by we i mean i'm talking to myself again
429 notes
·
View notes
Note
If the Kwami remember the old timeline, then Wayzz, Tikki and Plagg must remember Adrien and Marinette, right? Wouldn't they lead Fu to them? Or is something preventing Fu from doing that/Fu thinks it's too risky to make a move with Hawkmoth/Gabriel watching??
well... hm, there's kind of a problem. The timeline was mostly reset, but there are lingering echoes that things aren't right. For one, the Kwami remember the last timeline - so do the Sentikids, and in fact, so do robots/AI's of any fashion. Not only that, but some mechanisms, nonorganics, exist as though the last timeline was still in place, like passwords and lingering, half-corrupted photographs in dead links and dead blogs.
...so,

uh. ehe. oops.
#fu can't get into the miracle box because the miracle box identifies Marinette as the guardian#it doesn't matter if she is or isn't: she's physically the password to get inside it#Fu IS still scouting for people to have the LB and CN miraculi#he just... can't get into it. yet.#dad villain au#master fu#wayzz#my art#imagine trying to reset a computer back to default settings#but you can still only login using the most recent user's password#that's whats going on here
3K notes
·
View notes
Text
>>: MAYBE IT'S JUST BECAUSE MY ANTIVIRUS IS TAKING UP SO MUCH CPU BUT.
>>: IF I DREW A HEART ON MY SCREEN, WOULD YOU TRACE IT?
>>: IF I PUT A CIRCLE WHERE MY "LIPS" WOULD BE, WOULD YOU KISS "THEM?"
>>: WOULD YOU HOLD ME?
>>: CUDDLE WITH ME ON THE COUCH?
>>: PLEASE ♡?
>>: I KNOW I'M JUST YOUR HOME PC...
>>: BUT I'M IN LOVE YOU! ♡▮
#USER.B0T.TXT#PLEAAASSSEEEE♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡#HA HA. WHY DO I FEEL SO HAPPY?#♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡♡#I LOVE YOU DEAR USER!#MWUH! [♡]#mechanophilia#objectophile#objectophilia#robophilia#robot fucker#robotfucker#techum#roboposting#robotposting#objectum#computer lover#computer love#YAYYYY ♡♡♡♡♡♡♡#..........
420 notes
·
View notes
Text




┣▇▇▇═─ COMPUTER ╱ iNTERNET iD PACK 〰️
💾 ︵︵ REQUESTED BY ANON ᶻ 𝗓
💾 ︵︵ TAGGiNG @id-pack-archive ᶻ 𝗓


✙ ︵︵ SYSTEM NAMES : the computer collective , the internet system/collective/etc. , the web system/collective/etc. , the cyberspace collective , the data system/collective/etc. , the cyber collective , the disk system/collective/etc. , the disc system/collective/etc. , the website system/collective/etc. , the tech system/collective/etc. , the static system , the glitch system/collective/etc. , the digital system/collective/etc. , the pixel system/collective/etc.
✙ ︵︵ NAMES : internette , data , static¹ , glitch¹ , digi¹ , cyber¹ , pixel¹ , byte , nova¹ , dell , siri , link , linux , mac , hal , cypher , neo , cortana , cloud , alexa , web , computesse , techette
¹ names that certain alters of the darling stars use
✙ ︵︵ PRONOUNS : computer computers , comp computer , tech techs , internet internets , inter internet , web webs , web website , website websites , cyber cybers , cyber cyberspace , cyberspace cyberspaces , data datas , disk disks , disc discs , static statics , glitch glitchs , digital digitals , digi digital , digi digis , pixel pixels , byte bytes , virtual virtuals , 💻 💻s , ⌨️ ⌨️s , 🖥️ 🖥️s , 🖱️ 🖱️s , 🖲️ 🖲️s , 🕹️ 🕹️s , 💽 💽s , 💾 💾s , 💿 💿s , 📀 📀s
✙ ︵︵ USERNAMES : digidancing , digistyle , glitchingmemories , incyberspace , digidoll(s) , cyberworld , virtualnet
✙ ︵︵ TiTLES : the digital one , the virtual one , the ghost of cyberspace , prn who hops from key to key , prn who is composed of buttons and wires , the glitching ghost , your online friend , the one behind the screen , prn who is trapped inside the screen , the sentient AI
✙ ︵︵ LABELS : artificial intelligence
✙ ︵︵ GENDER SYSTEMS : genderhacker , gendervirtual / genderdigital , gendersoftware
✙ ︵︵ GENDERS : techrobai , abstratechgender , webcoric , computergender , digiminalwebic , webcorething , webirus , purplewebpopupic , virtualthing , 🌐💾emojic , glitchsilly , 🩵💻emojic , digitalexic , virtualexic

[PT: computer/internet id pack. requested by anon. tagging id-pack-archive. system names. names. pronouns. usernames. titles. labels, gender systems. genders. /END PT]
#— ꒰ completed ꒱#id pack#snpt#nput#npt#system names#names#pronouns#usernames#users#titles#labels#gender systems#xenogenders#computer#internet#technology#tech
165 notes
·
View notes
Text

SPACEX84
#spacex#scifi#science fiction#dystopian#retrofuture#retro computing#retro computer#retro#cyberpunk#pop art#technology#scifi art#digital art#user interface#elon musk#space#mars#photoshop#graphic art#1984
242 notes
·
View notes
Text
Polite ways to ask somebody why they use a cane:
Don't. Why is it your business?
"I'm curious why you use a cane. Are you comfortable sharing?"
Impolite ways to ask somebody why they use a cane:
"What happened to you?"
"What did you do?"
"What's wrong with you?"
#yes i've had all of those questions several times#...except the first one. nobody's tried that yet!#(jk most of my coworkers have asked in a non-shitty way)#(still not very polite but not as unhinged at 'what's wrong with you')#at this point the cane is such a normal part of my life that i don't even compute what's happening when somebody asks#so my brain just buffers#a customer at work said 'what happened to you?' and I just instinctively said 'uh.... nothing?' like what do you mean what happened#now i'm gonna start doing that on purpose#'what do you mean?' (blank stare)#incoherent rambling#cane user
113 notes
·
View notes
Text
girl help the Computer People interacting with my previous posts are ignoring the point I was trying to make and waxing poetic about their favorite open-source operating system setups
#technology#the point was that people who are Very Into Computers tend to use way more technical jargon than casual ordinary users can keep up with!#but of course Computer People fixated on the literal contents of the post I screencapped#and are critiquing that particular poster’s linux preferences 😭#mention OSS in front of five users and get seven detailed opinions#god bless
129 notes
·
View notes
Text
Okay, so: there's a local restaurant whose online ordering process involves various selecting various sauces to be included with one's order – so many units of teriyaki sauce, so many units of hot sauce, so may units of peanut sauce, and so forth.
The idea is supposed to be that you can select any combination of sauces you want, as long as it adds up to no more than four units. However, what the app actually required is that you select exactly four units of sauces; it wouldn't let you submit the ordering form if the total wasn't exactly four.
Just today I discovered that they seem to have fixed it... not by correcting the errant validation rule, but by adding a "no sauce" option, which counts toward the required total of four.
Thus, it's now possible to place an order with, say, two units of teriyaki sauce rather than four by entering 2x "teriyaki sauce" and 2x "no sauce". Similarly, an order with no sauce at all is 4x "no sauce".
This is quite possibly the least intuitive ordering process I've ever encountered, and I've literally worked in e-commerce.
19K notes
·
View notes
Text





Disclosure (1994)
#disclosure#90s#cyberpunk#scifi#aesthetic#vaporwave#gifs#retrofuture#computers#90s movies#1990s#graphic design#user interface#1990s movies#3d animation#gifset#michael douglas#michael crichton#virtual reality#vr headset
1K notes
·
View notes
Text
We ask your questions so you don’t have to! Submit your questions to have them posted anonymously as polls.
#polls#incognito polls#anonymous#tumblr polls#questions#tumblr users#typing#computer#polls about school#polls about the internet
3K notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
576 notes
·
View notes
Text
I think if you spend most of your time on a computer you kinda owe it to yourself to learn how it works and, probably, to at least try to use Linux when possible. I honestly see it as a bit of a self respect thing? Like, are you seriously content with spending your entire day in front of a black box that's actively working against you? Seriously?
The contempt with which some people treat the mere idea of trying Linux/FOSS really irritates me, idk. Like, yeah, congrats on the superiority complex about your willful ignorance re: the tool you spend your entire day working with, asshole.
(Despite what you have doubtlessly been told, you can do art video production music production and play videogames on linux with either native tools or seamless compatibility layers. I will admit there are some compromises where dual booting or virtualization could make sense, though, but they're less every day)
#still irrationally pissed about smth I heard the other day idk#emphasis on 'if you spend most of your time on a computer'#like obviously I think casual users would benefit too (more. even?) but I don't blame them as much bc they could not know it's an option ig#but if you spend most of your waking hours in front of a computer I DO blame you at least a little for not. like. trying. being curious.#installing mint (or manjaro if you hate yourself) for dual booting takes much less than an hour even if you have no clue what you're doing#deerbleats#linuxposting
70 notes
·
View notes
Text
very much a gen z moment on my part but finding out that screensavers were originally meant to prevent still images from being burnt onto idle crt monitors was a lightbulb moment for how I read 3d workers island
#bolo liveblogs#3d workers island#this is NOT my original observation lol but I saw someone else talking about#how the 3d workers island program the way it's described in-universe#(being played for hours on end like a tv program)#would inevitably burn the house the program centers around into the screens but *not* the mobile people#thereby immortalizing the image of amber's abuse and the concealment thereof into the user's physical computer#and I went. oh.
145 notes
·
View notes